Introduction
This procedure walks you thru a piecemeal installation of CentOS five.5. This procedure is performed victimization VMware digital computer seven.1.3 to host the guest software. Installation of CentOS during this procedure can occur in 5 distinct steps: 1) fitting the virtual drive; 2) partitioning the disk victimization CentOS Disk Druid; 3) playacting a default installation of CentOS five.5; 4) change CentOS; and 5) putting in Sysstat. the newest version of CentOS is downloaded free from the CentOS web site [1]. you'll get a 30-day trial of VMware digital computer from the VMware web site [2]. This piecemeal walkthrough is analogous to Robinson's glorious walkthough [9], however updated and with further detail on partitioning. a lot of careful installation directions is found within the CentOS documentation [3]. All references "[]" employed in this walkthrough ar listed below, within the References section. Good Luck!
Procedure
Step 1: fitting the Virtual Drive
VMware digital computer provides some handy options that well modify installation of common Linux distributions, like CentOS. VMware can acknowledge the Linux distribution, mechanically partition the virtual disk, tack it, so install Linux. the matter with VMware's automatic installation is that it's automatic disk partitioning routine might not partition the disk adequately, going light area in sure partitions for code installation. To avoid this downside at the point, this procedure can manually walk you thru manual configuration of the CentOS partitions before OS installation so as to make sure that the foundation partition has enough area for Jive installation. ensuing few steps show you the way.
Download the CentOS installation ISO [1] and burn to disk. Insert the CentOS installation disk within the drive.
From the File menu, purpose to New, so choose Virtual Machine... The New Virtual Machine Wizard seems.

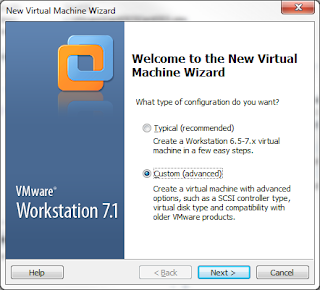
Select Custom, so click Next.

Accept the default digital computer, so click Next.

Select i will be able to install the software later, so click Next. this selection can possible already be elite for you.

On the Guest software, choose Linux; then, from the Version change posture list, choose CentOS; so click Next.

In the Virtual machine name text box, enter a name; then browse to the situation you wish to store this virtual machine; so click Next.

Accept the defaults, so click Next.

Accept the defaults, so click Next. one GB is over comfortable for a development machine.

For the needs of this procedure, the utilization bridged networking choices is chosen. However, any of the choices is also elite at this time. choose the choice most acceptable to your wants, so click Next.

Accept the default, so click Next.

Select the produce a replacement virtual disk possibility, so click Next.

Accept the default, so click Next.

Enter the scale of the virtual disk; check the allot all disc space currently option; choose the shop virtual disk as one file option; so click Next. For development functions, fifteen GB is over comfortable. it's easier to trace one computer file instead of multiple disk files for a given installation. Allocating all of the disc space at once simplifies future code installation.

Accept the default, so click Next.

Review the configuration choices you have got created, so click end. A progress meter can seem.

Once the disk has been created, VMware digital computer returns to the outline read for the newly-created VM.

Be sure your CentOS installation disk has been inserted into the table drive.
Check to form positive that the CD/DVD drive has been organized to purpose to the ISO image on the CentOS installation disk. To do this, 1st click Edit virtual machine settings, and then, on the Hardware tab, choose CD/DVD (IDE).

On the proper facet, make sure that the utilization physical drive possibility has been elite, so choose the acceptable drive from this option's list box. Click OK.
TIP: it is best to insert the CentOS disk within the drive at the start of VM setup, so step right into CentOS installation when fitting the VM. the rationale being that VMware digital computer can notice the installation disk within the drive throughout the VM setup method and afterward step right into launching the installation when beginning the VM.
Step 2: Launching the installation
Click Power on this virtual machine. VMware digital computer can mechanically notice the CentOS installation disk within the drive so launch the installation. Incidentally, you may conjointly see the VMware digital computer prompt, at rock bottom of the window. Ignore this for the present.

A prompt seems on prime of the CentOS installation screen. Click OK.

Click anyplace on the CentOS screen, so as to pass the mouse pointer awareness into the virtual machine, so press ENTER. make sure to try and do this quickly, as this selection doesn't stay for long. The installation preparation begins.

At some purpose throughout this preparation, you will be prompted to perform a CD take a look at.

Click anyplace on the blue half, press the Tab or right-arrow keys, so press ENTER. If you bought this way, there is no have to be compelled to take a look at the CDROM any longer.

The preparation can proceed for many minutes. once this part of the preparation is completed, a replacement screen can seem.

Click Next.

Select the language acceptable for you, or settle for the default, so click Next.

Select the keyboard layout acceptable for you, or settle for the default, so click Next.

Click Yes. This launches Disk non-Christian priest, and you will continue this procedure within the next section.

Step 3: Partitioning the Disk victimization CentOS Disk non-Christian priest
After the CentOS installation preparation routine finishes scanning the disk, it'll launch Disk non-Christian priest.
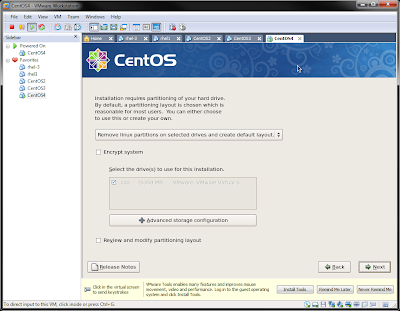
Click on the bar that states take away Linux partitions on elite drives and build default layout. a listing of many a lot of choices here are going to be displayed.
NOTE: consider references [5-7], below, for added useful detail on partitioning in Linux.

Select the list possibility produce custom layout, so click Next.

Click the New button. the primary partition you may produce is that the boot partition.

From the Mount purpose drop-down list box, choose /boot. confirm that the classification system kind shown is ext3. For the scale (MB), enter 100. Leave all different choices default. Then click Next.

Click the New button once more. ensuing partition you may produce is that the root partition. this is often wherever most of your applications are going to be put in to.

From the Mount purpose drop-down list box, select "/". confirm that the classification system kind shown is ext3. For the scale (MB), enter 8500. Leave all different choices default. Then click OK.

Click the New button once more.The next partition to make is that the swap partition. this is often wherever CentOS keeps its disk space - kind of like the Page get into Windows. Search the net for steerage on however massive this could be. For the needs of this procedure, you may set this to 1500, that with reference to takes care of the rest of the disc space accessible.

On the classification system kind drop-down list box, choose swap. For the scale (MB), enter 1500. Leave all different choices default. Then click OK. Lastly, the ultimate drive to make is that the /home drive, wherever user files ar hold on. Repeat the on top of procedures to make this drive, so click OK.

This completes disk partitioning victimization Disk non-Christian priest. Click Next.
Step 3: putting in CentOS
The next few steps involve preparative configuration before launching the particular installation of CentOS.

Accept the defaults, so click Next.

If you have got Dynamic Host Configuration Protocol organized on your network, make sure that the mechanically via DHCP possibility is chosen. Otherwise, tack as necessary. Then click Next.

Select town nearest you, leave all different settings as their default, so click Next.

Enter the foundation parole, so click Next. A progress meter can seem for a number of moments.

Now you're at the last preparation step.

Leave all settings at their default, so click Next.

Click Next. This launches the installation, that lasts many minutes. throughout the installation, you will be conferred with many completely different screens.


After many minutes, the installation are going to be completed. when installation is completed, you may be prompted to boot.

Click boot. hang on there! you are within the home stretch.

Click Forward.

If you wish to act with Windows systems over your network, check NSF4 and Samba. If you propose to create internet applications, check WWW and Secure WWW. For the needs of this procedure, i will be able to check simply WWW and Secure WWW. This opens those ports through the firewall to permit these services to control. Click Forward.

At the prompt, click Yes.

Click on the SELinux Setting drop-down list box, so choose Permissive [10]. Otherwise, you will not be able to install or run some applications. Then click Forward.

Check the modify kdump possibility. Leave the opposite choices here default. this can be helpful later if you wish to troubleshoot one thing later. Then click Forward. you will be prompted to verify the kdump possibility setting. Click okay to proceed.

Make the acceptable time adjusts PRN, so click Forward.

Enter a username, etc, so click Forward.

Accept the defaults, so click Forward.

Unless you have got a lot of code you wish to put in, simply click Forward.

Congratulations! If you've got reached the login screen, you've got with success put in and organized CentOS Linux. It remains to update your CentOS Linux instance with the newest upgrades and patches, and to put in one tool that you simply can notice helpful later which some applications need so as to be intsalled with success.
Step 4: change CentOS
At the CentOS login screen, login victimization the foundation account.

At this time, I performed AN install the VMware extras (that's what the prompt is for, down at rock bottom of the screen). As a result, the yellow prompt space at rock bottom of the screen can disappear.
Open a terminal. Enter the subsequent command [12]:
# yum update
This will mechanically verify what is updated, compile a listing of things needing update, transfer the updates from CentOS, so install them. it'll take many minutes for the update to complete. settle for the default in the least prompts.

This completes change of CentOS. Continue on to ensuing step.
Step 5: putting in Sysstat
Before you finally end up, there is one tool that it's helpful to put in before moving on to different things: sysstat [11]. you will find that it's required once putting in different applications, like Jive. sysstat is put in either through the CentOS Package Manager or from the program line. each ways are going to be conferred here. First, from the program line.
At the prompt, enter the subsequent command:
# yum list
This will cause an inventory to be generated of all doable applications and tools that you simply will install. Scroll through this list till you discover AN item starting with sysstat. it'll most likely look one thing like: sysstat.i386. observe of its entire name, so enter the subsequent command:
# yum install sysstat.i386
Note that your sysstat entry is also somewhat completely different from what's shown here. Once the installation begins, follow all prompts.

This completes insallation from the prompt victimization YUM. Next, victimization Package Manager.
From the Gnome panel, Applications menu, choose Add/Remove code. Then, on the Browse tab, within the left panel, choose Base System, so on the proper panel, choose System Tools

Click the optional packages button, so scroll down till you see the entry, sysstat-[version].i386, wherever your version could vary. choose this entry, check it, so click shut.

You'll be came back to the Package Manager tool. The Apply button are going to be enabled.

On the Package Manager tool, click Apply. you will be prompted to verify your picks.

Click Continue. A progress meter can seem momentarily.

...and then you will be au fait of the end result of the installation.

Click OK. you are came back to the Package Manager tool. Note that currently the Apply button is not any longer enabled.


































































